Featured articles
Latest articles
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.
Text Link.jpg)
.jpg)
.jpg)
Substring Matching over Field-Level Encrypted Data
Engineering
Substring Matching over Field-Level Encrypted Data
.jpg)
By
Nir Haas
January 1, 2025
Text Link


Agentic RAG Data Security Risks and Mitigations
AI Security
Agentic RAG Data Security Risks and Mitigations

By
Ariel Shiftan
December 30, 2024
Text Link


Comparing Dynamic Data Masking Proxy to Data Privacy Vault
Engineering
Comparing Dynamic Data Masking Proxy to Data Privacy Vault

By
Gil Dabah
October 25, 2024
Text Link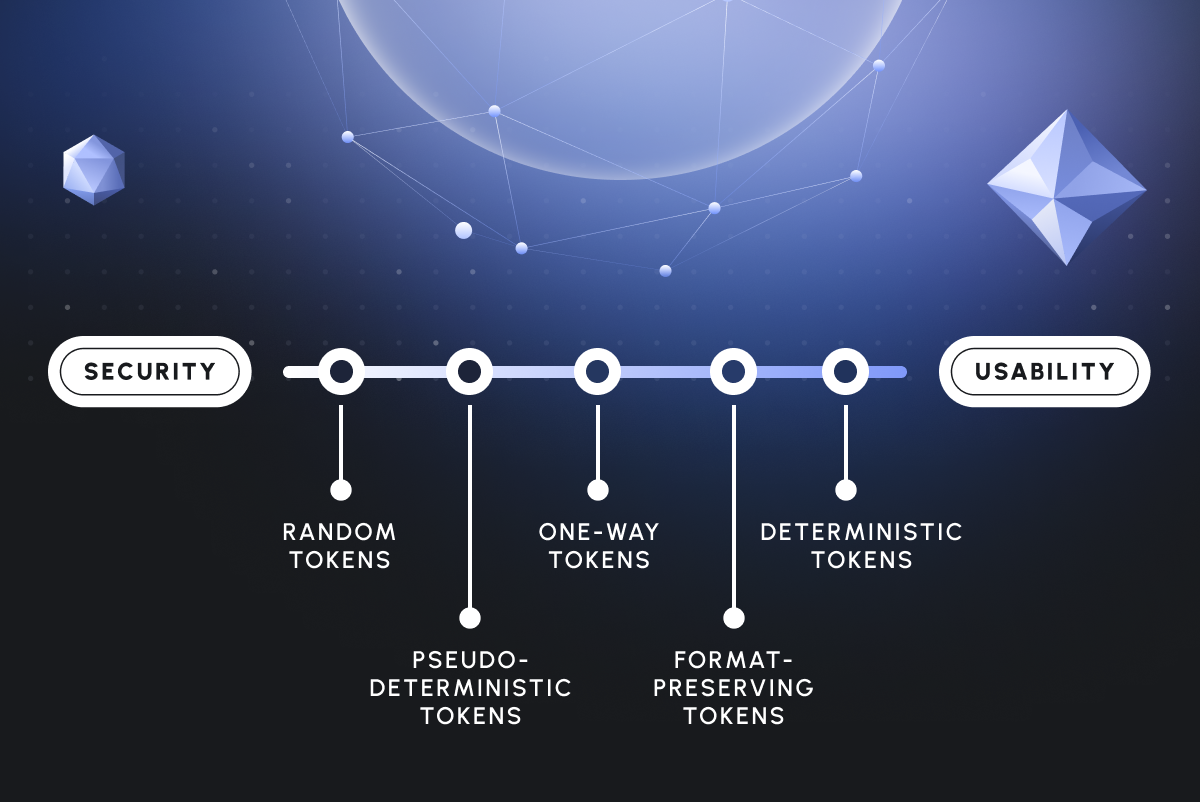


5 Tokenization Types Demonstrated Using Piiano Vault
Engineering
5 Tokenization Types Demonstrated Using Piiano Vault

By
Ariel Shiftan
September 19, 2024
Text Link


Why Spilling PII to Logs Is Bad and How To Avoid It
Engineering
Why Spilling PII to Logs Is Bad and How To Avoid It

By
Ariel Shiftan
September 2, 2024
Text Link


The Key Advantages of Data Privacy Vaults Over Traditional Databases
Security
The Key Advantages of Data Privacy Vaults Over Traditional Databases

By
Ariel Shiftan
August 1, 2024
Text Link


Understanding Encryption at Rest and Beyond: Strengths and Weaknesses
Security
Understanding Encryption at Rest and Beyond: Strengths and Weaknesses

By
Gil Dabah
July 30, 2024
Text Link


Use Piiano Vault to protect your customers’ secrets with encryption or tokenization
Privacy
Use Piiano Vault to protect your customers’ secrets with encryption or tokenization

By
Moty Michaely
July 17, 2024
Text Link


What is Application Level Encryption? Benefits & Implementation
Security
What is Application Level Encryption? Benefits & Implementation

By
Ariel Shiftan
June 27, 2024
Text Link


Automated Code Audits: Tools, Types, and Benefits
Security
Automated Code Audits: Tools, Types, and Benefits

By
Gil Dabah
June 20, 2024
Text Link


News - Piiano Achieves PCI DSS and SOC2 Certification
Security
News - Piiano Achieves PCI DSS and SOC2 Certification

By
Gil Dabah
June 3, 2024
Text Link


How to Protect Customers' Secrets in Your SaaS Offering: Detailed Guide
Privacy
How to Protect Customers' Secrets in Your SaaS Offering: Detailed Guide

By
Moty Michaely
May 3, 2024
Text Link


Piiano Vault Architecture – 60K RPS, 300 million rows, low latency w/PostgreSQL
Security
Piiano Vault Architecture – 60K RPS, 300 million rows, low latency w/PostgreSQL

By
David Erel
May 1, 2024
Text Link.jpg)
.jpg)
.jpg)
Introduction to Software Reverse Engineering [To Non-techies]
Security
Introduction to Software Reverse Engineering [To Non-techies]
.jpg)
By
Gil Dabah
April 24, 2024
Text Link


A New Emerging Data Security Category: AppSec for Data
Security
A New Emerging Data Security Category: AppSec for Data

By
Gil Dabah
April 1, 2024
Text Link


PCI DSS Compliance Checklist: The 12 Requirements [2024]
Security
PCI DSS Compliance Checklist: The 12 Requirements [2024]

By
David Erel
March 26, 2024
Text Link


How to Protect Personally Identifiable Information: PII Security Best Practices
Privacy
How to Protect Personally Identifiable Information: PII Security Best Practices

By
Gil Dabah
March 14, 2024
Text Link


What Is Data Leakage? Types, Causes & Prevention
Security
What Is Data Leakage? Types, Causes & Prevention

By
Gil Dabah
February 13, 2024
Text Link


Secure Sensitive User Profile Attributes in Auth0 (and other providers)
Privacy
Secure Sensitive User Profile Attributes in Auth0 (and other providers)

By
Moty Michaely
February 6, 2024
Text Link


Data Leak vs Data Breach: What's the Difference? [With Examples]
Security
Data Leak vs Data Breach: What's the Difference? [With Examples]

By
Gil Dabah
January 9, 2024
Text Link


The Rise in Threats to Personal Data: Takeaways from Apple’s Dec 2023 Report
Security
The Rise in Threats to Personal Data: Takeaways from Apple’s Dec 2023 Report

By
Ariel Shiftan
January 8, 2024
Text Link


How I Detected Sensitive Data Leaks, Such as Log Leaks in Open Source Projects Using Piiano Flows
Privacy
How I Detected Sensitive Data Leaks, Such as Log Leaks in Open Source Projects Using Piiano Flows

By
Guy Feigenblat
December 22, 2023
Text Link


Avoid Building Your Backend Applications with Encryption Failures
Security
Avoid Building Your Backend Applications with Encryption Failures

By
Gil Dabah
December 1, 2023
Text Link


Case Study: Data Sovereignty and Security Across Multiple Regions with Piiano Vault
Security
Case Study: Data Sovereignty and Security Across Multiple Regions with Piiano Vault

By
Gil Dabah
November 21, 2023
Text Link


What is Data Minimization? Main Principles & Techniques
Privacy
What is Data Minimization? Main Principles & Techniques

By
Gil Dabah
November 20, 2023
Text Link


Secure Social Security Numbers in 6 Simple Steps for Developers
Security
Secure Social Security Numbers in 6 Simple Steps for Developers

By
Ariel Shiftan
October 19, 2023
Text Link


Application Security Essentials for Protecting Data for Developers
Security
Application Security Essentials for Protecting Data for Developers

By
Gil Dabah
October 4, 2023
Text Link.webp)
.webp)
.webp)
PII Encryption: The Key to Protecting Your Customers’ Privacy
Security
PII Encryption: The Key to Protecting Your Customers’ Privacy
.webp)
By
Ariel Shiftan
September 5, 2023
Text Link


What is Data Tokenization? Everything You Need to Know
Security
What is Data Tokenization? Everything You Need to Know

By
Gil Dabah
August 25, 2023
Text Link.webp)
.webp)
.webp)
Exploring approaches to field-level encryption in Python for Django applications
Privacy
Exploring approaches to field-level encryption in Python for Django applications
.webp)
By
Imri Goldberg
August 1, 2023
Text Link


Column-Level Encryption 101: What is It, implementation & Benefits
Security
Column-Level Encryption 101: What is It, implementation & Benefits

By
Ariel Shiftan
June 20, 2023
Text Link


AWS KMS vs Piiano Vault: Which Encryption Mechanism to Choose for Your PII Data
Privacy Engineering
AWS KMS vs Piiano Vault: Which Encryption Mechanism to Choose for Your PII Data

By
David Erel
June 20, 2023
Text Link


The Importance of Key Rotation for Data Security
Security
The Importance of Key Rotation for Data Security

By
Ariel Shiftan
May 23, 2023
Text Link


What is Cloud Application Security? Challenges & Best Practices
Security
What is Cloud Application Security? Challenges & Best Practices

By
Ariel Shiftan
April 9, 2023
Text Link


Privacy by Design vs Security by Design: What’s the Difference?
Privacy
Privacy by Design vs Security by Design: What’s the Difference?

By
Gil Dabah
February 7, 2023
Text Link


Why Are Developers the New Data Protectors?
Privacy Engineering
Why Are Developers the New Data Protectors?

By
Gil Dabah
December 4, 2022
Text Link


Building vs. Buying a Data Privacy Vault to Protect Sensitive Data
Privacy Engineering
Building vs. Buying a Data Privacy Vault to Protect Sensitive Data

By
David Erel
November 30, 2022
Text Link


What Is a PII Digital Footprint and How to Reduce It
Privacy
What Is a PII Digital Footprint and How to Reduce It

By
Ariel Shiftan
November 17, 2022
Text Link


What is Data Protection & Why is it Important?
Privacy
What is Data Protection & Why is it Important?

By
Ariel Shiftan
October 27, 2022
Text Link


How to Secure Personally Identifiable Information: 3 Main Steps
Security
How to Secure Personally Identifiable Information: 3 Main Steps

By
Ariel Shiftan
August 25, 2022
Text Link


What Is PII Data and How Can You Protect It?
Privacy
What Is PII Data and How Can You Protect It?

By
Gil Dabah
August 9, 2022
Text Link


PII Protection Solution: How to Chose One, Threats & Solutions
Security
PII Protection Solution: How to Chose One, Threats & Solutions

By
Gil Dabah
August 4, 2022
Text Link


Golang Timeout Handling: 5 Practical Lessons
Engineering
Golang Timeout Handling: 5 Practical Lessons

By
Imri Goldberg
June 20, 2022
Text Link


How to Protect Social Security Number (SSN): Everything You Need to Know
Security
How to Protect Social Security Number (SSN): Everything You Need to Know

By
Gil Dabah
June 12, 2022
Text Link


How to Report a Data Breach: Step-by-Step Guide
Privacy
How to Report a Data Breach: Step-by-Step Guide

By
Ariel Shiftan
June 12, 2022
Text Link


Geeking Out On Privacy with TROPT
Privacy
Geeking Out On Privacy with TROPT

By
Gil Dabah
April 20, 2022
Text Link


Privacy by Design Checklist for Developers
Privacy Engineering
Privacy by Design Checklist for Developers

By
Ariel Shiftan
February 6, 2022
Text Link


History of Privacy: Past, Present & Predictions for the Future
Privacy
History of Privacy: Past, Present & Predictions for the Future

By
Gil Dabah
January 28, 2022
Text Link


Why Developers Should Join the Privacy Round Table
Privacy Engineering
Why Developers Should Join the Privacy Round Table

By
Gil Dabah
December 20, 2021
Text Link


How to Keep Personal Data Secure Online? Pseudonymize it
Privacy
How to Keep Personal Data Secure Online? Pseudonymize it

By
Ariel Shiftan
December 7, 2021
Text Link


The Black Shadow Case - a Zero Privacy Risk Alternative
Security
The Black Shadow Case - a Zero Privacy Risk Alternative

By
Ariel Shiftan
November 18, 2021
No articles found.
Join our newsletter
Get security and privacy best practices, tips, and news.
We care about your data in our privacy policy
Oops! Something went wrong while submitting the form.




Join our newsletter
Get security and privacy best practices, tips and news.
Your privacy is important to us, privacy policy.
Featured resources
See all resources







